The 5.2.3 release is a maintenance release and includes usability, security and performance improvements.
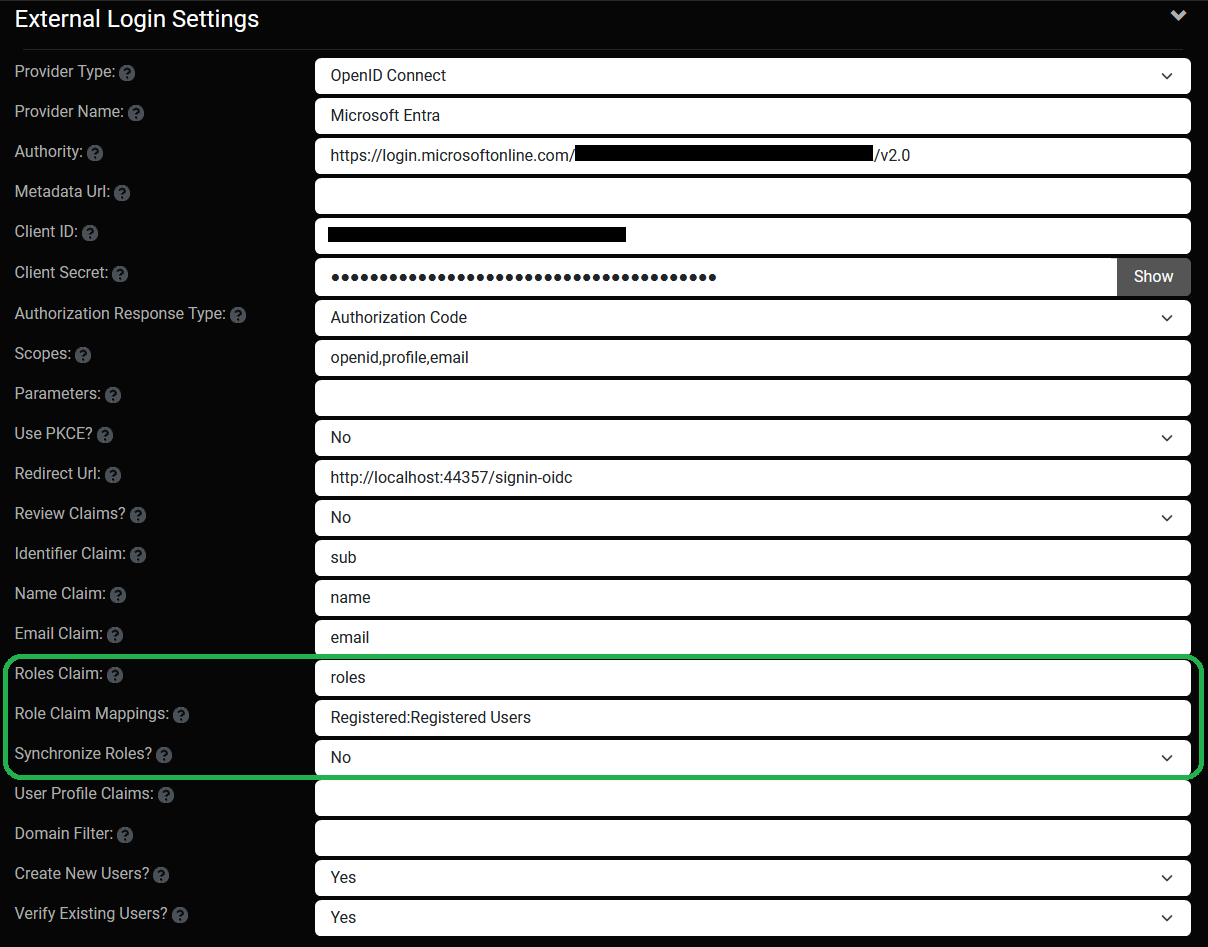
This release enhances the External Login capability with the ability to integrate Roles from an external identity provider (IDP). There are 3 options related to Role integration in the User Settings. The first is the Roles Claim which identifies the type name for the role claims which are passed by the IDP. The industry standard is for these claims to be named "roles" however the name can vary based on the configuration. The next option is the ability to optionally define your Role Claim Mappings. The default behavior in Oqtane is that any role assignments passed from the IDP will be automatically added to the user - with the caveat that the role names MUST already be defined in the Oqtane site. So if you have a role name of Editor in your IDP then you must have created a corresponding Editor role in your Oqtane site if you want those role assignments to be applied to users. In cases where the IDP role names do not exactly match the role names in your Oqtane site, you can define mappings. The last option is the ability to Synchronize Roles. Essentially this option allows you to treat the remote IDP as the source of truth for security roles, which means that any user role assignments which do not exist in the IDP will be automatically removed from the Oqtane site when a user logs in. Since this option requires aditional oversight and validation, it is not enabled by default. Note that Oqtane supports multi-tenancy so External Login can be configured independently for each site in an installation. The following is a sample configuration for Microsoft Entra.
Oqtane relies on the standard .NET Core Identity system for self-hosted authentication and authorization... and it extends this system with additional capabilities to support multi-tenancy. And in order to provide the best possible user experience, it utilizes an integrated suite of interactive razor components to satisfy all user scenarios. .NET Core Identity provides native support for a concept known as a Security Stamp which allows the system to keep track of all security changes to a user account. For example, if an administrator changes a user's password or removes role assignments from a user, the expected behavior is that the user should be immediately logged out of any active session and be forced to login again. This behavior is sometimes referred to as "logout everywhere" and is critical for managing access to privileged areas of a site. The Oqtane 5.2.3 release provides a number of enhancements in regards to security stamp support.
To date, the open source project has recorded over 2595 pull requests from 57 contributors and has published 47 official releases, which ranks it among the most active open source projects within the .NET Foundation. The Oqtane framework continues to evolve at a rapid pace to meet the needs of the .NET community. The 5.2.3 release is available for download on Github and is running in production at https://www.oqtane.org, https://www.blazorcms.net, and https://www.blazorkit.net.
